Entra Verified ID Explained: Why it’s the next BIG THING your business can’t afford to miss!
What’s all the hype about?
In today’s security-conscious technology landscape, trust is fast becoming the currency that will drive your business success! As cyber threats grow more sophisticated, and privacy concerns reach new heights, businesses are searching for innovative ways to secure their interests and build solid trust with their customers.
Enter Verified ID, a brand new, revolutionary approach to identity verification that’s poised to transform the way businesses operate. For a second, imagine a world where your customers can verify their identities securely, instantaneously, and without the need to expose unnecessary personal data. It’s a futuristic concept, but it’s something that’s happening right now.
So sit back and let us take you on a journey to explain what Verified ID is, how it works, and why it’s the next big thing your business can’t afford to miss!
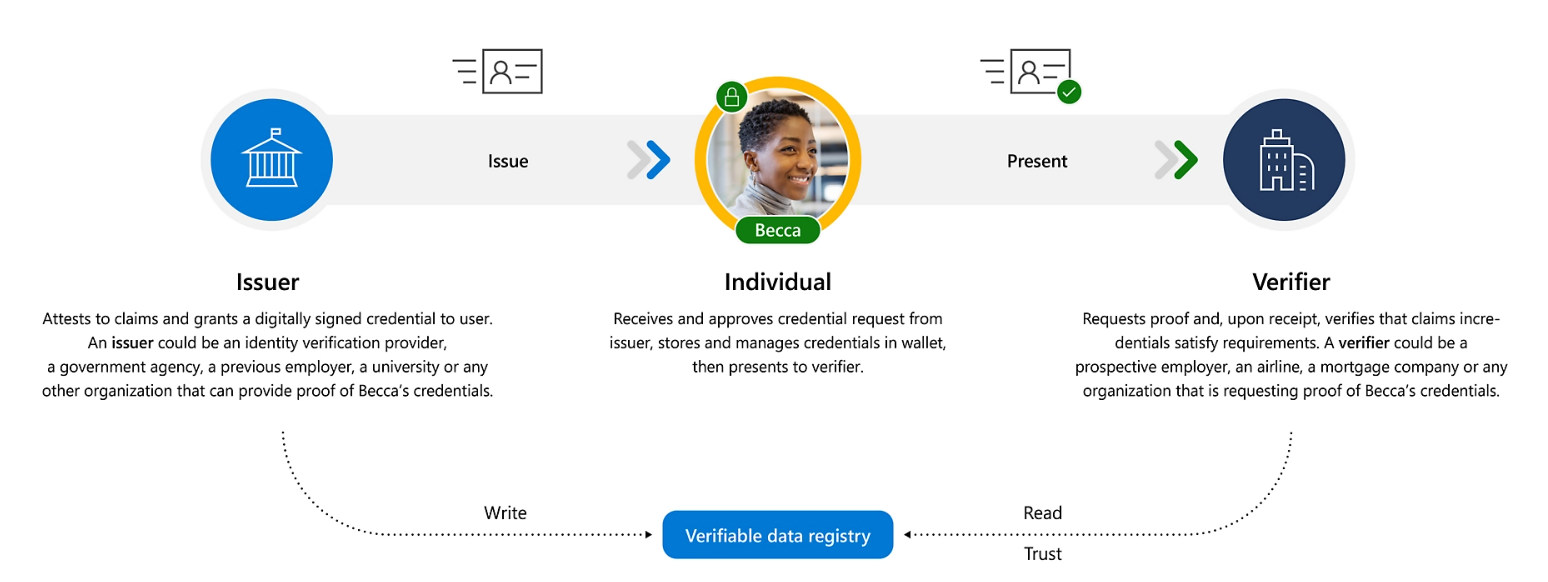
A picture is worth a thousand words.
Let’s start with the simple picture below to give you an idea of how it all ties together.
Issuer: Verified ID allows “Issuers”, such as government agencies, universities, or previous employers to attest to claims by granting a digitally signed credential to the user. A good example of this would be Vic Roads attesting to a user having a valid driver’s license.
User: The user or “Individual” can then store these verified credentials in a digital wallet and present them to anyone requesting verification as needed.
Requestor: The “verifier” or requestor can request proof and verify the claims that have been attested to by the “Issuer” providing a complete digital verification process at the click of a button.
What are the core components?
To get a complete understanding of how Verified ID works requires a look at all of the components at its core:
- Decentralized Identifiers (DIDs)
- Verifiable Credentials
- Digital Wallet
Decentralized Identifiers (DIDs)
At the heart of a decentralized identity like Verified ID is the concept of Decentralized Identifiers (DIDs). Unlike traditional identifiers (email addresses or usernames) that are issued and managed by central entities, DIDs are self-generated and owned by individuals. They are unique, persistent identifiers that don’t rely on a centralized registry or authority. They are typically stored on a blockchain or another decentralized ledger, ensuring they are tamper-proof and transparent. They also serve as the foundation for verifiable credentials, allowing users to prove their identity or other attributes without reliance on a third-party.
Verifiable Credentials
These are the digital equivalent of physical credentials, like a driver’s license or a university degree. However, unlike traditional credentials, verifiable credentials are cryptographically secure, decentralized, and privacy-preserving. A verifiable credential contains claims about an individual, such as their name, age, or qualifications, and is signed by the issuer’s private key. The individual or user can store these credentials in their digital wallet and present them when needed, allowing the recipient to check the authenticity of the credential using the issuer’s public key.
Digital Wallets
In the context of Verified ID, digital wallets are secure, personal storage apps where individuals can store their DIDs and verifiable credentials. The wallets are typically controlled by the individual, who can choose when and with whom to share their creds. Digital wallets provide a user-friendly interface for managing identities, making it easy for users to present creds and prove their identity in many contexts. Importantly, they also support selective disclosure, allowing them to share only the necessary information, enhancing privacy to another level.
How will my business benefit from it?
So, the short answer is “in so many ways”. Verified ID has a wide range of potential use cases and benefits, from employment verification to educational credentials and government services. Here are a few of the most promising and prominent applications for the technology.
Employment Verification
One of the most common use cases for Verified ID is employment verification. Employers can issue verifiable credentials to employees that will serve as proof of their employment status, job title, and other relevant information (like a verified business card). Employees can easily present these credentials when applying for loans, housing, or other services that require proof of employment. The approach is far more secure and efficient than traditional methods, which often involve manual checks and the distribution of sensitive information. With Verified ID, employees can prove their employment status without revealing any unnecessary personal info, and employers can automate the issuance and the entire verification process.
Education Credentials
Educational organizations can use Verified ID to issue verifiable credentials to students and grads. These credentials can include diplomas, transcripts, certificates, and any other academic achievements. Students can store these credentials in their digital wallets and present them to potential employers, other educational institutions, or any professional organizations. The verifier can easily validate the authenticity of the credential without needing to contact the issuer, significantly streamlining the application and verification process. This also helps reduce the risk of credential fraud because verifiable credentials are cryptographically secure and nearly impossible to forge.
Government Services
Governments can also use Verified ID to issue a wide range of verifiable credentials, like national IDs, driver’s licenses, Medicare, and more. These credentials can then be used to access government services, such as healthcare, voting, and other government services. By using Verified ID, governments can vastly improve the security and efficiency of identity verification processes, reduce the risk of identity theft, and enhance privacy for citizens. Individuals can manage their government-issued credentials in their digital wallets, choosing when and with whom to share their information.
How will Verified ID ensure your Identity is secure (the trust framework)?
At the heart of Verified ID is a robust “trust framework” designed to ensure that identities and credentials are both secure and trustworthy. The framework is made up of a combination of decentralized technologies, cryptographic techniques, and open standards to create a system where users can confidently manage and share their identity information. Let’s take a closer look at how the “trust framework” functions and why it holds the key to keeping your identity safe.
To sum it up, the “trust framework” is comprised of these core elements and concepts:
- A blockchain foundation
- Transparency and Trust
- Cryptographic Security
- Selective Disclosure
- Open Standards
Blockchain
The “trust framework” starts with Decentralized Identifiers (DIDs), which are stored on a blockchain or another fully decentralized ledger. Blockchain technology guarantees that these identifiers are tamper-proof, transparent, and immutable. Since the blockchain is decentralized, no single entity has control over the DIDs, significantly reducing the risk of fraud or manipulation.
Transparency and Trust
The decentralized ledger acts as a public record where DIDs and their associated public keys are stored. This transparency allows any verifier to check the authenticity of a credential by confirming that it was indeed issued by the trusted issuer’s DID. This process can occur end to end without revealing any sensitive information, maintaining and ensuring the privacy of the user.
Cryptographic Security
Every DID is associated with a pair of cryptographic keys, one public and one private. The private key is kept secure by the owner (the individual or organization that holds the DID), while the public key is published on the blockchain. When the issuer signs a verifiable credential, they use their private key, and the recipient of the credential can use the corresponding public key to verify the signature’s authenticity. This aims to ensure that verifiable credentials can’t be tampered with. If any attempt is made to alter the credential after it has been issued, the digital signature no longer matches, and the verifier would immediately know that the credential is not authentic.
Selective Disclosure
Another critical feature of Verified ID’s trust framework is selective disclosure, which allows users to share only the specific information necessary for verification. For example, if a user needs to prove they are over 18, they can share just that piece of information without revealing their full date of birth or other personal details. This capability is built into the cryptographic design of verifiable credentials, ensuring that privacy is a fundamental feature of the system and not just an afterthought.
Open Standards
Verified ID is built on open standards like the W3C’s Verifiable Credentials Data Model and the Decentralized Identifier (DID) standards, ensuring that the system is interoperable with other decentralized identity systems and allowing credentials to be used across many platforms and services. By adhering to open standards, Verified ID offers an ecosystem of trust where credentials issued in one system can be recognized and verified in another. This broad interoperability enhances
What an exciting time for businesses
With all of this in mind, just imagine the endless possibilities Verified ID can offer your business. If you are ready to take your digital identity management to the next level, B2Six specialises in implementing cutting-edge Microsoft solutions like Verified ID. Get in contact today to learn how we can tailor a Verified ID solution to meet your unique business needs and keep you ahead of the curve. Let’s explore how we can make your identity systems more resilient and future-proof. Reach out now!”
250 +
Successful Projects
30 +
Years of Experience
50 +
Service Offerings
See what our
Clients are Saying.
We engaged B2Six Team to provide the technical expertise and automation tools to migrate one of our strategic customers. They were incredibly knowledgeable and flexible, and their automation tools made the entire process seamless.
Oreta
Customer
B2Six has been a NAB delivery partner for more than 5 years, providing project and professional services. Their deep technical expertise has allowed NAB to move at pace in its simplification journey.
NAB
Customer
What stood out for us with B2Six is consistent quality of people (proficient in the domain and has significant Customer environment knowledge) and deliverables. Everyone from B2Six demonstrated a ‘can do attitude’ and you have been focused on delivering a good outcome over the commercials. Often this meant, you maintained flexibility, with strategic partnership in mind.
Large Australian Retailer
